Vice Society is a ransomware group that has been wreaking havoc across the education, manufacturing and medical sectors, among others. Since its emergence in 2021, the group has targeted hundreds of victims worldwide, demanding ransom payments as high as $1 million USD. In 2022 alone, Vice Society leaked the data of over 100 companies on their blog. However, apart from a flashy Grand Theft Auto-inspired logo, there is nothing special about this ransomware group. They have been characterised as a prime example of how unsophisticated, mediocre threat actors can find great success in the ransomware ecosystem by relying on others for the development of tools to conduct their attacks. The group’s evolution demonstrates why ransomware continues to be one of the top threats facing organisations globally, while their victims reveal the unfortunate state of cybersecurity and lack of cyber preparedness – particularly across education institutions, healthcare providers and government bodies.
This blog will provide a deep dive into Vice Society; their emergence and early history, most notable attacks, infection chain, tactics, techniques and procedures (TTPs), profile, and motivations. Finally, recommendations and best practices will be offered to help organisations protect themselves against similar ransomware threats.
First sightings and notable 2021 developments
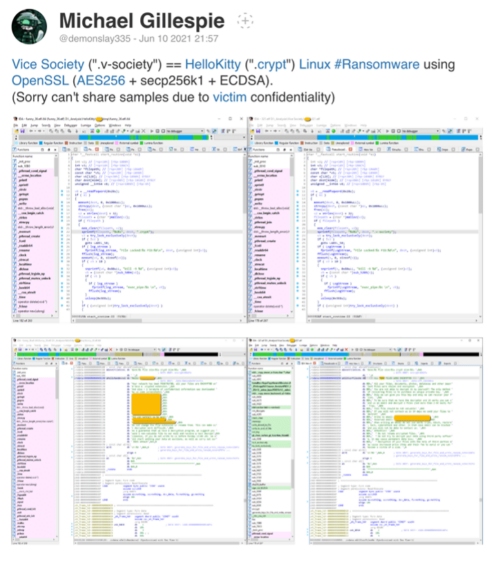
The first public reports of Vice Society emerged in June 2021 on Twitter, when security researchers such as Michael Gillespie noticed that the payloads of another ransomware strain, Hello Kitty, were appending a .v-society extension to encrypted files.
Shortly after, the actors behind the Vice Society ransomware operation launched their own leak site. One of the first data leaks was related to an attack against the Whitehouse Independent School District in Texas. In this incident, over 18,000 files containing data of former employees, dependents and students were leaked, including names, addresses and social security numbers. The threat actors stated that they chose to leak the data after the school district ignored their messages and refused to pay the ransom – a pattern that is seen in their later attacks.
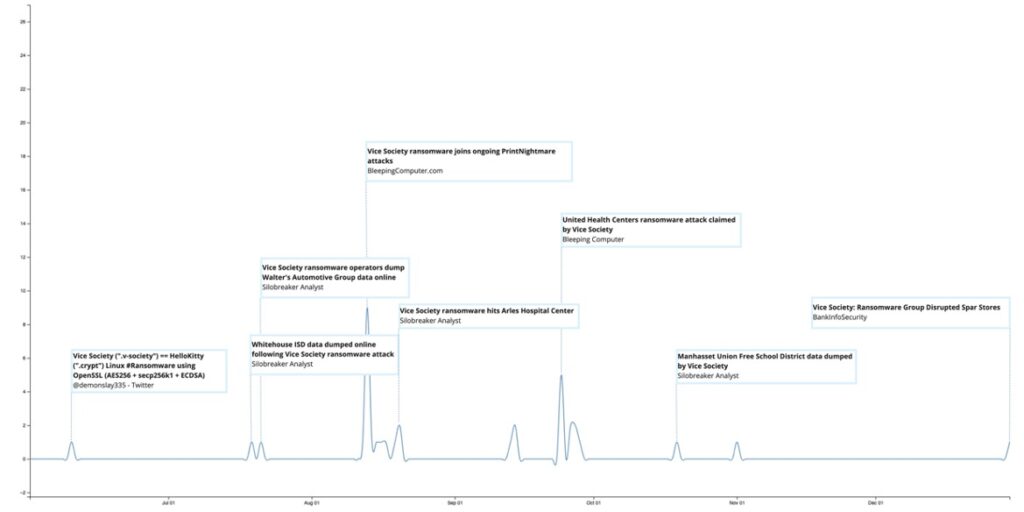
In August 2021, Cisco Talos observed Vice Society exploiting PrintNightmare, a vulnerability in Microsoft Windows. The group continued their spree of attacks, focusing on healthcare institutions such as the Eskenazi Health Centre and Barlow Respiratory Health Centre in Indiana, the Arles Hospital Centre in France and the United Health Centre in California. In October, Vice Society hit the Manhasset Union Free District in New York, leaking data after the district’s ransom payment offer was deemed ‘too low’. It finished off the year with an attack against Spar stores in the UK. Our analysis of posts on their leak site revealed that in 2021, the group targeted victims from a variety of different sectors, including education, oil and automotive, as well as local municipalities, government organisations, health centres and hospitals.
2022: Vice Society makes the news
In 2022, Vice Society ramped up their activities, attacking colleges, hospitals and even the Argentina Senate. The group also rebranded themselves, using a new logo inspired by Grand Theft Auto.
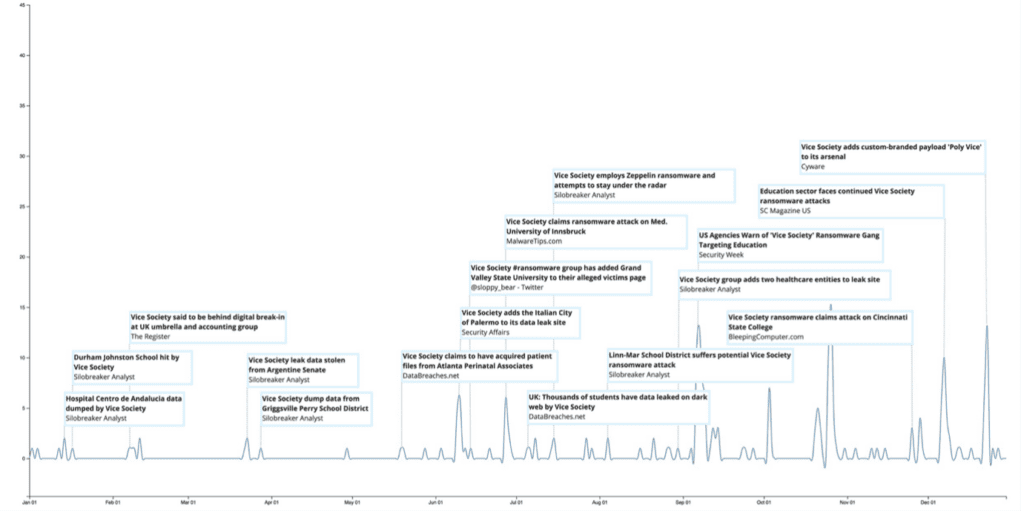
Halfway through the year, their attacks became more frequent, with 14 new victims added to the leak site in June. These included the Grand Valley State University in Michigan, the Medical University of Innsbruck and the Italian City of Palermo. Throughout the first half of the year, Vice Society continued to use Hello Kitty ransomware as their primary payload. However, in June, researchers noticed the deployment of a different payload – Zeppelin ransomware. Towards the end of 2022, the group further added variants such as BlackCat, QuantumLocker and RedAlert to their arsenal.
In September 2022, CISA, the FBI and MS-ISAC released a joint advisory warning of Vice Society’s attacks against the education sector – over a year after the first public reports. The same day the advisory was issued, the operators claimed an attack against the second-largest school district in the United States – the Los Angeles Unified School District (LAUSD). The district’s data wasn’t leaked until a month later, in October, after they refused to pay the ransom and worked with CISA to restore their systems. In response, Vice Society warned their victims against working with agencies and law enforcement if they wanted to avoid their data being leaked online.
Throughout September and October, the group conducted further attacks against education institutions, which seemed to correlate with the start of the academic year. In October, it was reported that in several instances, Vice Society threatened to leak stolen data without encrypting it. The group wrapped up 2022 with more attacks against UK schools and US colleges such as the University Institute of Technology in Paris, Xavier University in Ohio and SOAS University in London. Other targets included IKEA stores in Morocco and Kuwait. They were also seen using a new custom-branded ransomware payload dubbed ‘PolyVice’. Based on similarities with other ransomware such as SunnyDay and Chily, researchers believe that PolyVice was most likely created by a developer selling custom-branded payloads to multiple ransomware operators.
2023 incidents so far
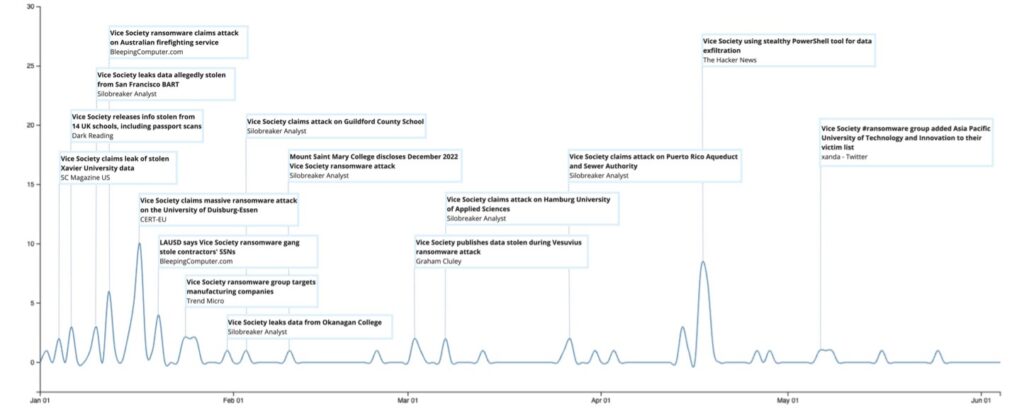
Vice Society started off the year with a bang by adding the San Francisco Bay Area Rapid Transport (BART) to their data leak site on 6th January. This was followed by data leaks from the Victoria Fire Department in Australia and the University of Duisburg-Essen, one of the largest universities in Germany. In line with their previous behaviour, the group leaked the University’s data months after the attack took place when the victim refused to give in to their demands.
The education sector continued to be a target, with Okanagan College in Canada, Guildford County School in the UK, Mount Saint Mary College in the US and the Hamburg University of Applied Sciences added to Vice Society’s list of victims in February and March.
One of their most recent high-profile activities was an attack against CommScope, the US network infrastructure provider serving a range of customers including hospitals, schools and US federal agencies.
In early April 2023, Vice Society was observed using a custom-built PowerShell script to exfiltrate data from victims.
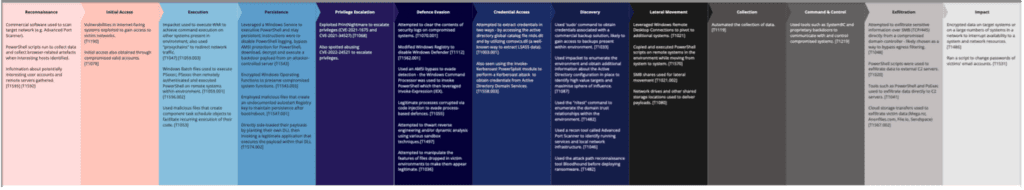
Infection chain and MITRE ATT&CK mapping
Over the years, Vice Society has continuously evolved and updated their tools and methods, becoming an increasingly sophisticated threat. The following mapping of their TTPs across each stage of the MITRE ATT&CK framework has been compiled based on research by CISA, Unit 42, Microsoft and Cisco Talos.
View Full Vice Society MITRE ATT&CK Mapping
Victims by sector and geography
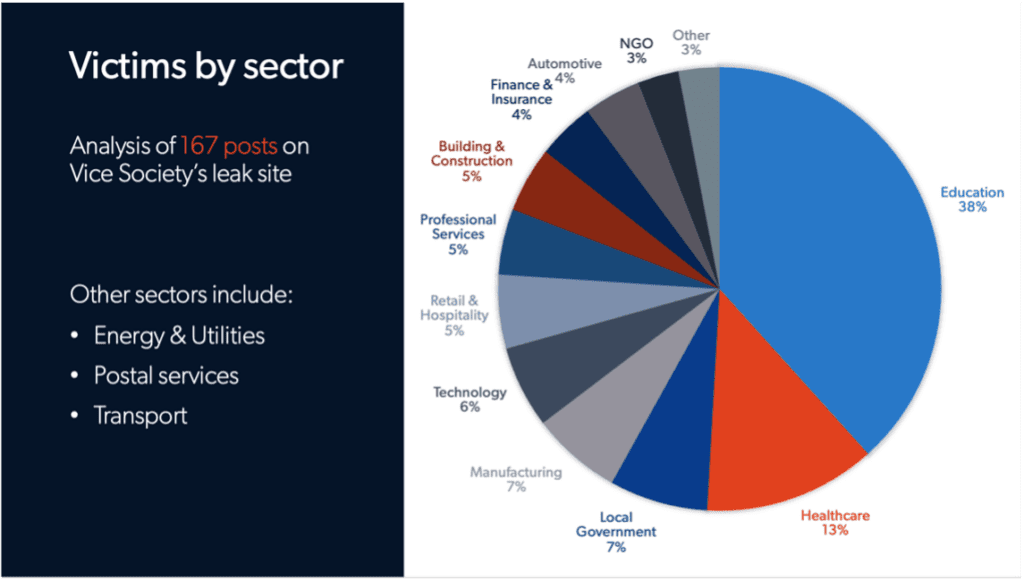
The primary sector Vice Society has targeted is education, which represents around 40% of their victims. Secondary sectors include healthcare, state and local governments, manufacturing, professional and legal services, wholesale, and retail.
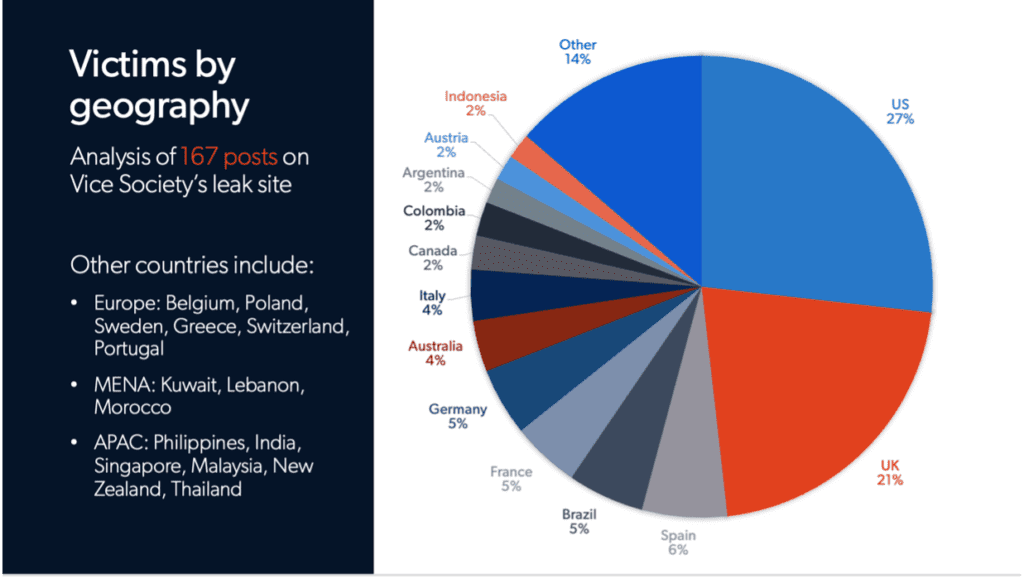
Almost half of all victims are from the UK and US, but they have targeted organisations across the globe. In the US, the top targeted states include California, Texas, Pennsylvania and Wisconsin.
Profile and motivations
Following the attack on United Health Centers in September 2021, BleepingComputer reached out to Vice Society, asking them why they target schools and hospitals – this was their response:
“Why not? They always keep our private data open. You, me and anyone else go to hospitals, give them our passports, share our health problems etc. and they don’t even try to protect our data. They have billions of government money. Do they steal that money?
USA president gave big amount to protect government networks and where is their protection? Where is our protection?
If IT department don’t want to do their job we will do ours and we don’t care if it hospital or university.”
Vice Society is opportunistic and financially motivated as they’re willing to wait to see if ransom can be negotiated. Researchers have observed initial demands as high as $1 million USD, with final demands as high as $460,000 USD. On average, the final ransom demand decreases by approximately 60% compared to the initial demand. As described earlier, they typically leaks data when the victim is unresponsive, refuses to pay out, offers a ransom payment that is too low or works with authorities.
Finding success in mediocrity
The amount of time that expired between the first instances of Vice Society activity being detected and the joint advisory is striking. Despite targeting schools, hospitals and even hospices, it took 15 months for the ransomware group to receive public attention from law enforcement agencies.
There are several reasons why ransomware groups like Vice Society want to stay under the radar. Firstly, keeping a low profile means less attention being paid to them by law enforcement and thus a lower risk of being identified and prosecuted. Secondly, less publicity decreases the amount of attention from security researchers, which means less time spent on analysing their behaviour, methodology and other characteristics whose exposure could lead to them being exposed. Lastly, ransomware attacks on hospitals, hospices and other facilities whose disruption could lead to the loss of life have been seen as controversial even among cybercriminals. Dodging the attention of threat actors could limit the risk of them being targeted by other cybercriminals. However, over the past year, Vice Society has not shied away from larger targets – as was evident from the LAUSD or CommScope attack. They have also been featured on researcher blog posts mentioning them as one of the top 2022 ransomware threats on their own leak site. They seem to be gaining confidence and together with their constant evolution and further sophistication of tools, it is unlikely they will disappear any time soon.
How to stay ahead of ransomware threats
A proactive and comprehensive approach to defending against ransomware attacks is critical. Vice Society serves as a good example of why organisations shouldn’t rely on a single source to inform them of potential risks they could be faced with and should have the tools and capabilities needed to pick up on incidents before they become major threats. This requires looking at a wide range of sources – news reports, research, blog posts, as well as underground forums and cybercriminal channels. Furthermore, understanding the fuller picture can provide security practitioners with the confidence they need to make decisions to prioritise vulnerability management and efficiently allocate resources to fix gaps in their security posture.
Proactively approaching threats can also help organisations stop attacks at an early stage before significant damage and disruption are caused. By leveraging external threat intelligence, organisations can gain a more comprehensive understanding of what the infection chain looks like, how to detect the attack when it occurs and how to identify the stage of the attack and halt its effects.
Moreover, as we saw with Vice Society, threat actors continuously evolve their tactics, which requires organisations to keep track of changes and developments in their campaigns and take appropriate measures to maintain their preparedness against these attacks. Continuously gathering intelligence on ransomware attacks can help organisations put effective and up-to-date incident response plans in place.
Tackling a complex, ever-changing threat landscape is a challenge all security practitioners face, often finding themselves in a position where it is hard to prioritise what to focus on first. However, even with opportunistic cybercriminals like Vice Society, patterns can be spotted. Focusing on those who have been known to target your industry in the past can be a good starting point, and having the tools and capabilities in place to pick up on these patterns in external reporting is critical. Click here to learn how you can unlock actionable intelligence faster.