
Enhanced threat identification
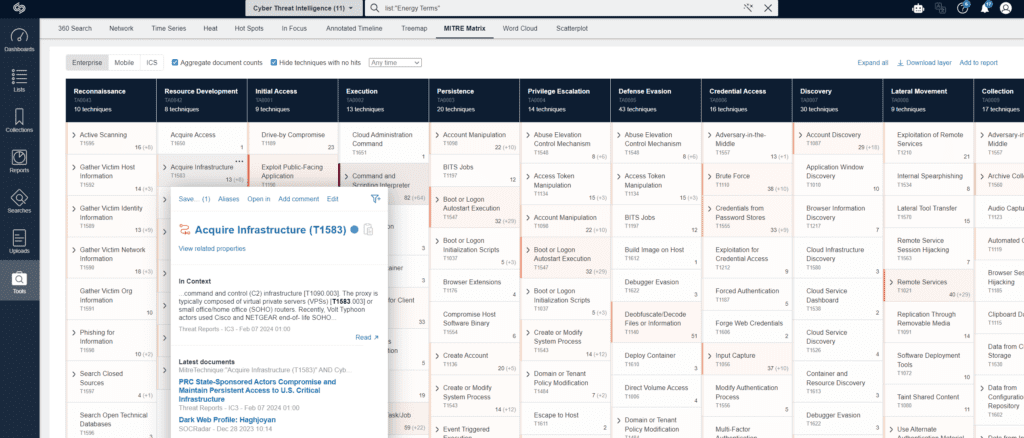
The integration of the ATT&CK® framework, entity support for Tactic and Technique identifiers, and a MITRE Matrix visualization tool makes it easier to identify threat actors and malware TTPs across open source and finished intelligence datasets.
Monitor the evolving threat landscape
Security teams can monitor and prioritise TTPs labelled with ATT&CK identifiers, providing improved visibility of the evolving threat landscape in a single platform. Seamlessly populate an ATT&CK Matrix for Enterprise, ICS or Mobile, based on real-time findings.
Better informed, proactive decision-making
Silobreaker’s report workflow, alerting, and MITRE ATT&CK® Navigator compatible layers streamlines manual tasks and facilitates the dissemination of high-quality intelligence to multiple stakeholders, enabling better-informed decision-making and proactive defence against adversaries.
