What is the MITRE ATT&CK?
MITRE ATT&CK stands for MITRE Adversarial Tactics, Techniques and Common Knowledge. It is a globally accessible knowledge base, developed and maintained by the non-profit MITRE Corporation. It is a curated collection of cybersecurity information that is regularly updated by MITRE, with input from the global cybersecurity community, to ensure it is accurate and useful.
MITRE ATT&CK catalogues the tactics, techniques and procedures (TTPs) used by cybercriminals throughout the cyberattack lifecycle –from initial information gathering to attack execution. This information helps security teams simulate cyberattacks to test defences, develop effective security policies, controls and incident response plans, and select and configure security technologies for better threat detection and prevention.
MITRE ATT&CK matrices
The MITRE ATT&CK matrix is the core component of the MITRE ATT&CK framework. The matrix categorises adversary TTPs used in cyberattacks and is presented as a table with columns representing different tactics used by attackers (e.g., Initial Access, Persistence, Defence Evasion). Each tactic represents a specific goal adversaries aim to achieve during an attack.
Within each tactic column, there are several rows detailing individual techniques used to achieve that tactic.
MITRE ATT&CK has multiple matrices, each focusing on the specific tactics and techniques relevant to different environments or platforms. The three primary matrices are:
- Enterprise Matrix – The most widely used matrix and focuses on TTPs used to target enterprise networks and systems like Windows, macOS and Linux
- Mobile Matrix –Focuses on TTPs used to compromise mobile devices and applications
- ICS Matrix – Focuses on TTPs used to attack Industrial Control Systems (ICS), critical for infrastructure like power grids and water treatment plants
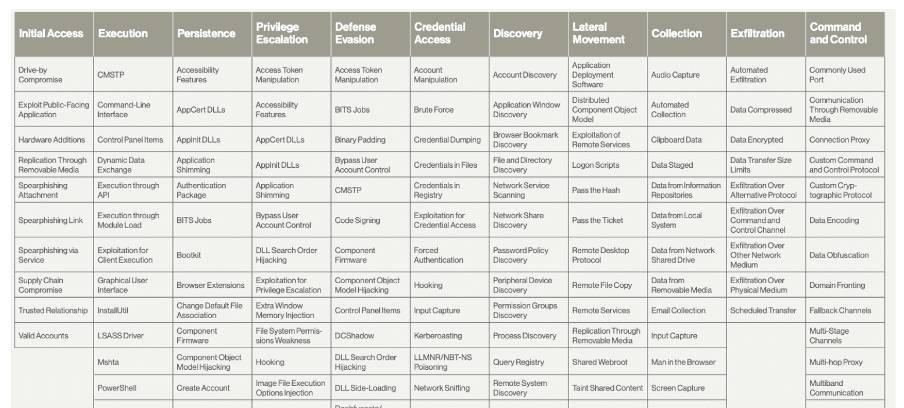
By covering different platforms and operating systems (e.g., Enterprise, Mobile, ICS), the MITRE ATT&CK matrices allows security professionals to focus on the TTPs most relevant to their specific environment.
MITRE ATT&CK tactics
In the MITRE ATT&CK framework, tactics are the “why” behind an attacker’s actions. They describe the high-level objectives that adversaries are trying to achieve throughout the cyberattack lifecycle. Tactics don’t delve into the specifics of how attackers achieve their goals. They focus on the objectives themselves.
MITRE ATT&CK tactics are typically arranged to reflect the different stages of a cyberattack, from the initial reconnaissance phase to data exfiltration and impact.
These may vary slightly across different matrices, but the common MITRE ATT&CK tactics used in cyberattacks include:
- Reconnaissance – Gathering information about the target network or system
- Resource development –Acquiring the tools and resources needed for the attack
- Initial access – Gaining initial access to the target network or system
- Execution – Running malicious code on the target system
- Persistence –Maintaining access to the target system for long-term operations
- Privilege escalation –Gaining higher privileges within the target system
- Defence evasion – Avoiding detection by security tools and techniques
- Credential access – Stealing or compromising user credentials
- Discovery – Finding valuable data on the target system
- Lateral movement –Moving from one compromised system to another within the network
- Collection – Gathering the stolen data from the target system
- Command and control (C2) – Communicating with the compromised system to control it remotely
- Exfiltration – Transferring the stolen data out of the target network
- Impact – Causing damage or disruption to the target system or organisation
By understanding the attacker’s mindset and motivations, security teams can better predict attacker behaviour, focus defences to address the tactics most relevant to their environment and improve threat detection.
Techniques in the MITRE ATT&CK framework
In the MITRE ATT&CK framework, techniques represent the “how” behind an attacker’s actions. They describe the specific methods and procedures adversaries use to achieve the goals outlined in the MITRE ATT&CK Tactics (the “why”).
Techniques delve deeper than tactics, detailing the concrete steps attackers take to infiltrate, manipulate or steal data from a system. Each tactic can have multiple associated techniques, reflecting the diverse ways attackers can achieve their goals. As attackers develop new methods, new techniques are continually added to the MITRE ATT&CK knowledge base.
For example, if the attacker’s tactic is Initial Access (gaining initial entry into a system), numerous techniques could be associated with this tactic, such as phishing emails, exploiting software vulnerabilities or brute-force password attacks.
Understanding techniques allows security teams to proactively identify specific attack vectors to focus on, helping them to develop targeted detection strategies and implement appropriate mitigation measures to block those specific techniques.
Each description in the MITRE ATT&CK techniques list typically includes:
- Unique Identifiers – A code assigned to the technique for easy reference
- Clear Explanations – A detailed description of how the technique works
- Detection methods – Recommendations on how to identify systems being targeted by this technique
- Mitigations – Strategies to prevent or minimize the impact of this technique
- References – Links to additional resources for further information
By understanding both tactics (the attacker’s goals) and techniques (the methods used), security teams gain a comprehensive picture of the attacker’s approach. This knowledge empowers them to develop a more robust defence strategy and proactively protect their systems from cyberattacks.
MITRE ATT&CK use cases
The MITRE ATT&CK Matrix supports a variety of use cases for enhancing cybersecurity operations. Some of the key ways a security team can leverage MITRE ATT&CK include:
- Enhancing cyber threat intelligence – By integrating MITRE ATT&CK with threat intelligence feeds, security teams can enrich their understanding of adversary TTPs, leading to more informed and proactive defence strategies
- Threat hunting – Security analysts can utilise MITRE ATT&CK to conduct threat hunting, leveraging detailed information on adversary TTPs to identify threats that may have bypassed existing defences
- Red teaming and adversary emulation – MITRE ATT&CK provides a framework for simulating real-world cyberattacks that allows security teams to test the effectiveness of their defences, uncover vulnerabilities and refine their incident response plans
- Alert triage and investigation – MITRE ATT&CK can help in the prioritisation and investigation of security alerts, with security solutions like SIEM (Security Information and Event Management), UEBA (User and Entity Behaviour Analytics), EDR (Endpoint Detection and Response) and XDR (Extended Detection and Response) incorporating MITRE ATT&CK data to streamline alert triaging and trigger automated incident response
- Security gap analysis and planning – Organisations can use MITRE ATT&CK to conduct a comprehensive security gap analysis, identifying weaknesses in their current cybersecurity posture and planning targeted improvements
- SOC maturity assessment – Organisations can assess the maturity of their Security Operations Centre (SOC) using MITRE ATT&CK, evaluating how well their SOC can detect, respond to and mitigate cyber threats with minimal manual intervention
- Stakeholder communication – The common language and standardised taxonomy provided by MITRE ATT&CK facilitate clear and concise communication about cyber threats and defences with stakeholders, consultants and vendors
The various use cases for MITRE ATT&CK help organisations optimise their security operations, improve their overall security posture and stay ahead of evolving cyber threats.
Cyber Kill Chain vs. MITRE ATT&CK
Both Cyber Kill Chain and MITRE ATT&CK are frameworks used in cybersecurity, but they approach understanding cyberattacks from different angles. Lockheed Martin’s Cyber Kill Chain focuses on the stages attackers typically go through during a cyberattack.
It provides a high-level overview of the attack lifecycle, typically consisting of seven stages: Reconnaissance, Weaponisation, Delivery, Exploitation, Installation, Command and Control and Actions on Objective.
The Cyber Kill Chain doesn’t provide specific details about the techniques attackers use at each stage. It also doesn’t account for the possibility of attackers skipping or re-ordering stages.
MITRE ATT&CK focuses on the TTPs used by attackers throughout the cyberattack lifecycle. It provides a more granular view of attacker behaviour, with a comprehensive database of tactics and techniques. Each technique is clearly defined and includes details on detection methods and mitigations. MITRE ATT&CK is a more dynamic framework, constantly updated with new techniques as they are discovered.
The Cyber Kill Chain is a good starting point for organisations defining their cybersecurity strategy and provides a clear, concise model for communicating cyber threats to less technical audiences. The MITRE ATT&CK model is more valuable for experienced security professionals who need to understand the specifics of attacker behaviour, improve threat detection and mitigation strategies and develop targeted security controls.
While they have different focuses, the Cyber Kill Chain and MITRE ATT&CK can be used together effectively. The Cyber Kill Chain provides a high-level overview, while MITRE ATT&CK fills in the details with specific techniques used at each stage. This combined approach offers a comprehensive understanding of cyberattacks and empowers security teams to develop a more robust defence strategy.
FAQs
What is the MITRE ATT&CK framework?
The MITRE ATT&CK framework is a globally used framework in cybersecurity that enables organisations to understand how cyber attackers operate. It serves as a knowledge base, documenting the tactics, techniques and procedures (TTPs) that attackers typically use across various stages of cyberattacks.
By providing a common language for discussing cyber threats, the framework fosters collaboration and information sharing among cybersecurity professionals. The MITRE ATT&CK framework allows organisations to better understand attacker behaviour in order to prioritise their defences and implement more effective detection strategies to counter potential threats.
The MITRE ATT&CK framework is a living document, continuously updated by MITRE, and security professionals around the globe, with new adversary techniques as they emerge. This ensures defenders stay informed and prepared for evolving cyber threats.
What are the 3 main matrices of the MITRE ATT&CK framework?
The MITRE ATT&CK framework offers three main matrices, each focusing on a distinct attack landscape:
- Enterprise Matrix – The most widely used, targeting tactics and techniques used to compromise corporate networks and systems (Windows, macOS, Linux, etc.)
- Mobile Matrix – Details TTPs specifically designed to exploit mobile devices and applications
- ICS Matrix – Concentrates on threats targeting Industrial Control Systems (ICS) critical for infrastructure like power grids and water treatment plants
What does MITRE stand for?
The name MITRE is not an abbreviation. Despite various theories suggesting what the word MITRE stands for, the company itself confirms that it is not an acronym. Over the years, the name has been stylised in both uppercase and normal capitalisation.
MITRE was started in 1958 with support from the U.S. Air Force to connect the academic research community and industry in designing the Semi-Automatic Ground Environment, or SAGE, an important system for air defence during the Cold War.
In 2013, MITRE developed ATT&CK, a freely accessible knowledge base of adversary tactics and techniques based on real-world observations, now used globally.
What is the use case of MITRE ATT&CK framework?
There are a variety of use cases for the MITRE ATT&CK framework. It can be used to:
- Enhance threat intelligence by integrating with threat feeds to understand adversary tactics
- Drive threat hunting using detailed adversary tactics for proactive threat detection.
- Support red teaming by guiding simulate real-world attacks to assess defences
- Optimise alert triage, helping to prioritise and investigate security alerts
- Analyse security gaps by identifying weaknesses for targeted improvements
- Assess SOC maturity, evaluating readiness to mitigate cyber threats
- Facilitate communication, standardising language for clear threat discussions
The MITRE ATT&CK framework can be used in many ways to help organisations improve security operations and stay ahead of cyber threats.
How to use ATT&CK using Silobreaker
Silobreaker provides powerful insights on emerging risks and opportunities in real-time, enabling global enterprises to make intelligence-led decisions to safeguard their business from cyber, physical and geopolitical threats, mitigate risks and maximise business value.
By integrating MITRE ATT&CK® TTP detections into its threat intelligence platform, Silobreaker enhances threat visibility and response capabilities, leveraging extensive data sources to categorise and assess threats based on real-world observations.
Threat intelligence analysts often struggle to transform raw information and reporting into actionable intelligence. Silobreaker’s MITRE ATT&CK® TTP integration enables them to zero in on TTPs across open and premium intelligence sources, filtering by source, activity, volume and timespan. Analysts can seamlessly populate a dynamic, up-to-date ATT&CK Matrix for Enterprise, ICS or Mobile domains.
Organisations can discover TTPs from Silobreaker’s unparalleled collection of critical threat intelligence sources, including open-source blogs, government agencies, threat research, social media and premium vendors like Mandiant, Flashpoint and Intel 471 – all presented in the ATT&CK Matrix view. This breadth of coverage ensures access to the latest and highest-quality information on TTPs, all in one place.
ATT&CK identifiers are integrated into Silobreaker’s entity extraction and querying capabilities, allowing analysts to use tactic or technique identifiers to search for relevant threat actors, malware or industries. Intelligence teams can efficiently disseminate TTP intelligence to key stakeholders through custom reports and the Silobreaker intelligence workspace.
Find out how Silobreaker’s threat intelligence platform, enhanced with MITRE ATT&CK® TTP detection capabilities, can help your organisation gain greater visibility of the evolving threat landscape and stay ahead of emerging risks.
