Ransomware attacks have long plagued the healthcare sector, in fact the first known ransomware incident specifically targeted the healthcare sector when Joseph L. Popp distributed 20,000 infected floppy disks to attendees of the World Health Organisation’s international AIDS conference in 1989. Since then, ransomware attacks have become increasingly sophisticated, with attackers targeting medical devices, networks, servers, PCs, databases, and medical records, as well as vulnerabilities in systems used by healthcare entities. Recent ransomware incidents against Change Healthcare, Synnovis, and Lurie Children’s Hospital have highlighted the devastating impact cyberattacks can have on healthcare institutions, whilst also exposing their vulnerabilities and the lack of adequate defensive measures currently in place. Consequently, the rate of ransomware attacks on the healthcare sector will likely continue to increase unless healthcare organisations implement more proactive and pre-emptive strategies to combat ransomware.
Modern Ransomware Trends in the Healthcare Sector
Since 2018, there have been 743 confirmed ransomware attacks on healthcare organisations globally, with the average daily downtime costing approximately $900,000, establishing ransomware as a significant threat to the healthcare sector. Out of 922 publicly reported ransomware attacks in 2023, Silobreaker reported that 177 were directed at the healthcare sector, 137 of which targeted the United States. Despite ransomware actors historically demonstrating a reluctance to target the healthcare sector, the opportunity for significant financial gain has likely contributed to the increase in attacks against the sector in recent years. Consequently, the increasing frequency and financial impact of ransomware attacks has put immense pressure on healthcare organisations, with many struggling to adapt to this growing threat. Specifically, St. Margaret’s Health in Spring Valley, Illinois, became the first hospital to permanently close in June 2023, partly due to the financial strain caused by a ransomware attack.
Notable Ransomware Actors targeting the Healthcare Sector
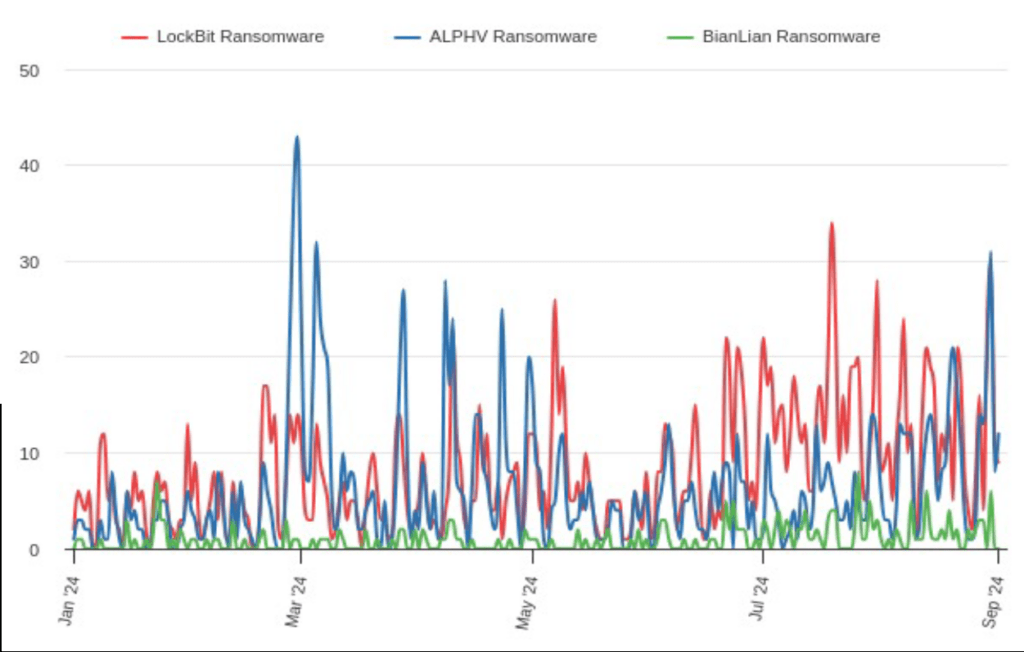
Among the most active ransomware groups targeting the healthcare sector are LockBit 3.0, ALPHV, and BianLian. The top MITRE ATT&CK tactics, techniques, and procedures (TTPs) shared between these actors are phishing (T1566), valid accounts (T1078), remote services (T1021), service stop (T1489), and data encrypted for impact (T1486).
ALPHV Actor Profile
Also known as BlackCat, the ALPHV ransomware group was active since approximately December 2021 and, along with LockBit 3.0, was the most active RaaS operation targeting the healthcare sector until its exit scam in March 2024. Following calls from ALPHV’s administrator encouraging its affiliates to target hospitals, the healthcare sector became the most common amongst ALPHV’s leaked victims from December 2023. ALPHV have carried out multiple notable attacks on the healthcare sector, including attacks on Change Healthcare, Jewish Home Lifecare, Valley Health Network, and more.
LockBit 3.0 Actor Profile
LockBit 3.0 similarly first emerged as the leading ransomware-as-a-service (RaaS) provider targeting the healthcare sector in 2023, accounting for over 30% of all reported attacks. Despite its temporary disruption in early 2024, LockBit 3.0 still carried out multiple significant ransomware attacks against the sector, including attacks on Hospital de Canne Simone Veil, Community Clinic of Maui, the University Hospital Centre Zagreb, and more.
LockBit 3.0 employs a modular approach, encrypting its payload until execution, which enhances its ability to evade detection and complicate malware analysis. The ransomware uses multiple methods for initial access, including exploiting Remote Desktop Protocol (RDP), phishing, exploiting vulnerabilities in public-facing applications, drive-by compromises, and abusing valid accounts. For data exfiltration, LockBit 3.0 uses the custom Stealbit exfiltration tool, previously used with LockBit 2.0, as well as tools such as Rclone and publicly available file-sharing services such as MEGA.
BianLian Actor Profile
The BianLian ransomware group, first identified in 2021, has evolved into a highly sophisticated threat, shifting from encryption-based attacks to a data extortion model in 2023. The group poses a significant threat to the healthcare sector, with attacks on the sector accounting for 18.3% of all observed BianLian attacks since the start of 2024. BianLian uses a multi-stage attack strategy that begins with phishing emails containing malicious attachments or links to compromised websites. The group also gains initial access to networks by leveraging compromised RDP credentials, likely acquired from initial access brokers or phishing. BianLian uses a custom backdoor written in Go, as well as remote management access software, such as TeamViewer and AteraAgent, for persistence and C2 communication, Cobalt Strike for network reconnaissance, and Rclone for data exfiltration.
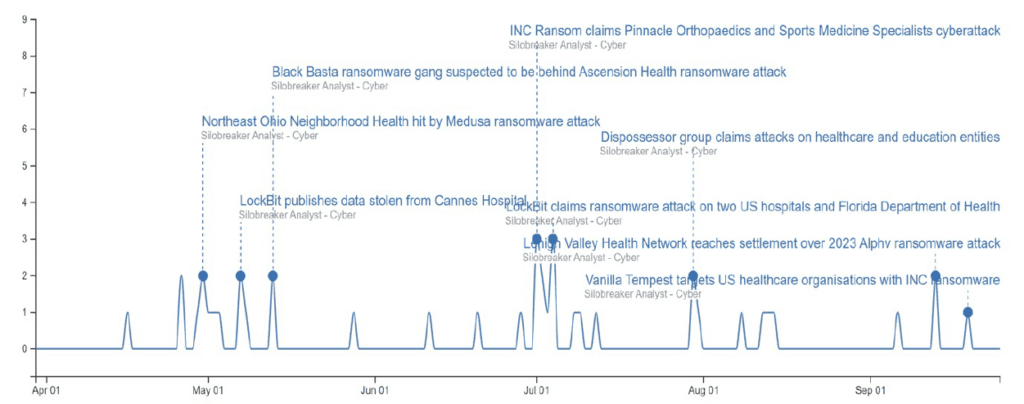
Notable Ransomware Attacks Against the Healthcare Sector
Change Healthcare
On February 21st, 2024, the US healthcare technology company disclosed it suffered a cyberattack that caused widespread network disruptions. More than 100 critical applications were affected, including systems related to dental, pharmacy, medical records, clinical services, patient enrolment, engagement, revenue, and payment services. The attack prevented patients from accessing medications and medical services, with many healthcare providers, including Northeast Ohio Neighborhood Health and the Department of Veteran Affairs, impacted by the attack. UnitedHealth CEO Andrew Witty later disclosed that the ransomware attack was orchestrated by ALPHV. The group exploited a critical vulnerability in Citrix NetScaler, commonly referred to as CitrixBleed, compromising remote login credentials for a Citrix portal at Change Healthcare that lacked multi-factor authentication (MFA).
On June 20th, 2024, UnitedHealth Group, Change Healthcare’s parent company, confirmed that the breach also involved the theft of sensitive patient information. The stolen data included health plans, insurance policy details, member and group IDs, medical record numbers, providers, diagnoses, claims and payment data, Social Security numbers, and more. The personal and health information of US military personnel was also stolen, posing a serious threat to national security as nation-state adversaries could potentially exploit the data for strategic purposes.
Despite paying a ransom to the attackers, $22 million according to ALPHV, data stolen from Change Healthcare was eventually leaked online – but by another group, calling itself RansomHub. The gang claimed responsibility for a second ransomware attack on Change Healthcare and the theft of 4TB of data on April 8th, 2024. By this point, ALPHV had officially shut down in a move many saw as an exit scam. Rumours quickly emerged that RansomHub may be a rebrand of ALPHV, or alternatively made up of former ALPHV affiliates, who decided to leak the stolen data after feeling defrauded by ALPHV following the exit scam.
The attack on Change Healthcare not only jeopardised the privacy of millions but also presented a serious risk to national security. Furthermore, the failure to implement basic cybersecurity measures such as MFA highlights systemic vulnerabilities within the healthcare sector, which could lead to future attacks. Finally, UnitedHealth’s payment of a ransom sets a dangerous precedent, potentially encouraging future ransomware against the healthcare sector.
Synnovis
On June 3rd, 2024, the UK blood test management organisation disclosed it was affected by a ransomware attack, made possible by the exploitation of a zero-day vulnerability, that impacted all of its IT systems and resulted in interruptions to many pathology services. Specifically, NHS London disclosed that the incident significantly impacted the delivery of services at Guy’s and St Thomas’ NHS Foundation Trust, King’s College Hospital NHS Foundation Trust, as well as primary care services in Southeast London. The ripple effects of the attack were significant, as more than 3,000 hospital and GP appointments were delayed, impacting over 900,000 individuals.
The Qilin ransomware gang claimed responsibility for the attack, stating that it was a deliberate act of revenge on the UK government’s actions in an undisclosed war. On June 20th, 2024, Qilin posted almost 400GB of allegedly stolen data allegedly stolen from the ransomware attack to its leak site, including patient names, dates of birth, NHS numbers, descriptions of blood tests, and business account spreadsheets. Qilin demanded a $50 million, though Synnovis refused to pay the ransom.
The ransomware attack on Synnovis had significant implications for both healthcare operations and patient privacy and has highlighted the vulnerability of healthcare infrastructure to cyberattacks. Moreover, Qilin’s claim that the attack was motivated by geopolitical tensions underscores the increasing use of cyberattacks as tools for political retribution. Synnovis’ refusal to pay a ransom highlights the ethical dilemma organisations face between mitigating immediate damage and discouraging future cyberattacks.
Ann & Robert H. Lurie Children’s Hospital of Chicago
On February 1st, 2024, the US hospital disclosed it was actively responding to a cybersecurity incident that forced it to take its network systems offline. The incident impacted the hospital’s internet, email, phone services, and access to its MyChat platform. Many of the hospital’s scheduled procedures were also delayed by the incident as the hospital was forced to triage emergency situations in a first-come, first-served approach. It was only in May 2024 that Lurie Children’s Hospital was able to reactivate patient-facing systems.
The Rhysida ransomware group claimed responsibility for the attack by adding Lurie Children’s Hospital to its darknet leak site. The group reportedly exfiltrated 600GB of sensitive data, including names, addresses, Social Security numbers, health claims information, health plan, medical conditions, or diagnoses, and more, pertaining to more than 791,000 individuals. Rhysida offered to sell the alleged stolen data for 60 Bitcoin (approximately $4 million) , unless a ransom was paid. The hospital was advised against paying a ransom following which Rhysida claimed to have sold the stolen data.
The ransomware attack on Lurie Children’s Hospital raises profound ethical concerns – or a lack of them by the attackers, especially given the nature of the institution. Targeting a hospital that cares for children, many of whom may be facing life-threatening conditions, presents a moral dilemma, as the attack not only compromised sensitive medical data but also disrupted critical care.
Lessons Learnt – Why do Ransomware Actors Target the Healthcare Sector?
Several factors have contributed to the healthcare sector becoming such a popular target for ransomware attacks, including a lack of adequate security measures and cybersecurity expertise, mostly due to insufficient funding, as well as the troves of valuable confidential data organisations in the sector hold.
Healthcare providers increasingly rely on IT and Internet of Things (IoT) systems to deliver digital healthcare services. However, many of these technologies were not designed with security in mind, leaving significant vulnerabilities in place. Medical devices, although vital to modern healthcare, often have security weaknesses that are difficult to protect or update. This problem is exacerbated by healthcare institutions operating vast networks of legacy infrastructure, including outdated IoT systems that have reached end-of-life status. These systems are difficult to patch, and since healthcare services need continuous uptime to treat patients, applying critical updates can be delayed, creating ideal conditions for cyberattacks. Compounding the issue, according to ENISA, only 23% of healthcare organisations had a dedicated ransomware program in 2023, reflecting widespread under-preparedness to counter the growing ransomware threat.
Financial constraints equally play a key role in the healthcare sector’s vulnerability to ransomware attacks. Healthcare systems often lack the necessary funding to overhaul and secure their IT infrastructure. Without adequate resources to upgrade outdated systems or implement advanced security measures, healthcare providers remain exposed to cyber threats. This gap in cybersecurity investment makes it easier for ransomware groups to exploit vulnerabilities, knowing that many healthcare organisations cannot afford the necessary defences.
Entities in the healthcare sector are also frequently targeted as they store vast amounts of sensitive patient data, including medical records, personal information, and payment details. This data is extremely valuable to threat actors, as it can be used for identity theft, insurance fraud, or other malicious activities. The confidential nature of this data means that healthcare providers are often more willing to pay ransom demands to prevent leaks, making them attractive targets for ransomware groups. In fact, healthcare organisations are not only more likely to pay a ransom but many paying more than the initial demand, with Sophos reporting that 57% of healthcare organisations paid more than the initial request.
Another reason ransomware actors target the healthcare sector is the strain on its workforce and lack of cybersecurity expertise. Healthcare workers are already overwhelmed by heavy workloads, long hours, and high-pressure deadlines, so introducing cybersecurity protocols into their daily routines adds another layer of complexity that many staff members cannot accommodate. Moreover, most medical professionals lack the expertise to identify and mitigate cyber threats, making the sector particularly vulnerable to human error, such as opening malicious attachments in phishing emails or falling for social engineering attacks. To reduce risks without overburdening staff, any new security measures must be streamlined and seamlessly integrated with existing systems. Providing essential cybersecurity training is also essential to help staff recognise and prevent potential threats. Simple countermeasures could include performing routine backups of critical systems and using strong passwords in combination with MFA. While preventing ransomware attacks against the healthcare sector may seem daunting and time-consuming, Silobreaker can help automate the monitoring and detection of these threats. Our platform enables organisations to identify new ransomware threats and stay ahead of commonly exploited vulnerabilities. By keeping you informed about the latest threats and disruptions, Silobreaker can empower healthcare providers to enhance their cybersecurity posture and ensure continuity of care. To learn more about how Silobreaker can protect your organisation from ransomware attacks please get in touch here.

