Over 20 years ago, Mandiant released one of the first reports that publicly named an advanced persistent threat (APT) group – APT1. APT1 was deemed to be one of China’s most persistent cyber threat actors and was specifically attributed to the People’s Liberation Army Unit 61398. The group carried out cyber espionage activity against more than 100 companies across 20 major industries.
The report itself became a vehicle of change within the cyber threat intelligence community to encourage information sharing amongst vendors and security practitioners, particularly around nation-state actors and APTs. Despite the positive aspect of information sharing, biases in reporting on nation-state actor activity in open-source, mainstream media have since become a challenge.
In a recent Silobreaker blog post, Kevin Tongs highlighted many types of biases that can happen in intelligence production. These may lead to bad decisions, missed opportunities and security breaches. Amongst these biases are the ruling theory and confirmation bias, which, in the case of reporting on nation-state actor activity, may lead to an exaggerated focus on activity originating from historical ‘enemies’. At the same time, these biases might also influence us and the media to ignore or downplay activity coming from allies.
A historical bias focusing on China, Iran, Russia and North Korea
In general, Western mainstream media tends to more frequently cover cyber incidents attributed to China, Iran, Russia and North Korea, and provide less coverage of cyber activity by Western nations. This is not surprising, as many of the campaigns attributed to nation-state hackers from these countries target Western nations and would directly pose a security risk to them. Nonetheless, it is commonly known that Western countries also actively engage in cyber operations against other nations, be they offensive or defensive in nature. However, public reporting of such events rarely makes it into mainstream media. This could pose a challenge for security practitioners who rely on open-source data, especially those seeking to understand the full spectrum of nation-state activity across the world.
With this in mind, we chose to examine a recent campaign that stood out to us, as it received little reporting from mainstream Western media.
Operation Triangulation: Limited coverage in Western media
The campaign, dubbed Operation Triangulation, targeted the government sector and used a novel zero-day exploit, something that we assumed would normally receive mainstream media attention. Whilst the exploitation of Apple zero-days typically makes it into mainstream media almost instantly, this was not the case for Operation Triangulation. The campaign was first reported on in June 2023 by Kaspersky, who discovered a new zero-click exploit in Apple iOS that had been deployed on the devices of dozens of its employees. The campaign involved the novel spyware implant, TriangleDB, which was used to escalate privileges and harvest user information.
The campaign is not believed to be specifically targeting Kaspersky, with Russia’s Federal Security Service (FSB) stating that thousands of iPhones belonging to diplomatic missions and embassies in Russia were also infected. The FSB attributed the campaign to the National Security Agency and further alleged that Apple had closely collaborated with the US to develop the exploit, though they did not provide any evidence. Apple denied any involvement in developing the exploit and subsequently fixed the vulnerabilities.
Amongst researchers and cyber threat publications, the campaign received some coverage. Over the last 90 days, there were a total of 182 reports on the campaign from global cyber threat publications. These publications are a collection of sources from around the world that produce independent research focusing on cyber threat intelligence.
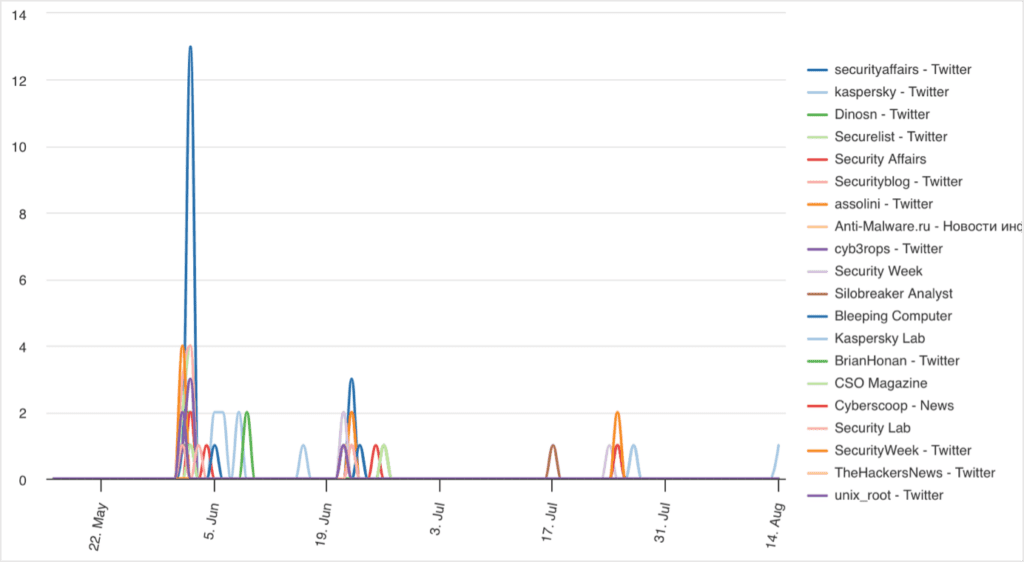
It should be noted that some of the top reporting sources are Kaspersky, who are based in Russia and were the ones who discovered the campaign in the first place.
In comparison, there was far less reporting on the campaign from mainstream Western media. Specifically, there were just 31 reports on the campaign from news sources in the United States, the United Kingdom, Canada, Australia and New Zealand (Five Eyes). These sources are a collection of news outlets from the Five Eyes countries that focus on general news.
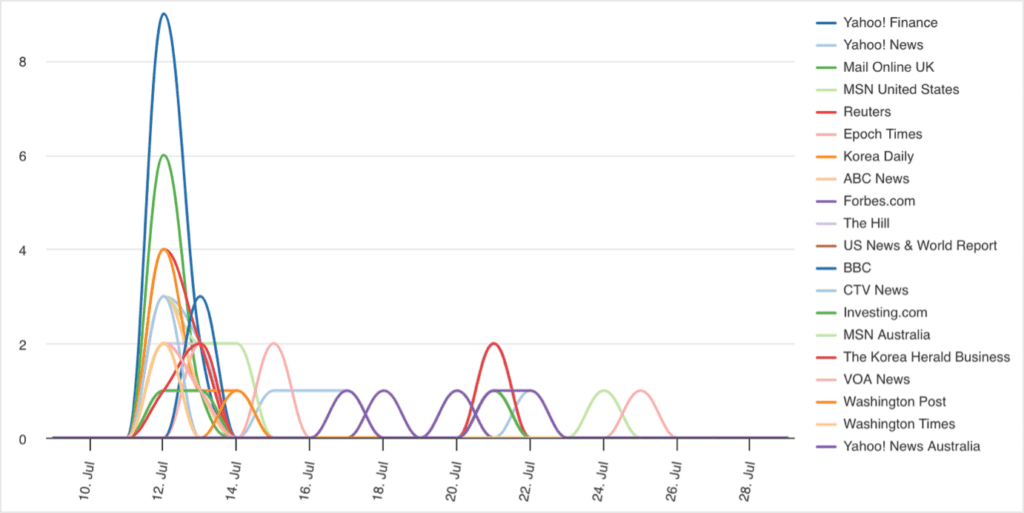
It is not particularly unexpected that sources dedicated to covering cyber activities would provide more coverage than general news sources. However, it is still significant that the cyber threat publications have over 500% as much coverage when compared to mainstream media from the Five Eyes countries. It is especially notable since the cyber threat publications our investigation focused on comprise less than 800 sources, compared to nearly 10,000 Five Eyes news sources.
After observing this difference in reporting, we looked at a similar type of campaign to see whether mainstream Western media would similarly have little coverage compared to the cyber threat publications.
Pegasus spyware: Recent activity receives less media attention
The difference in the amount of reporting became more apparent when looking at a different campaign that has some similarities to Operation Triangulation – the exploitation of iOS zero-days to deploy Pegasus spyware. The spyware, developed by the NSO Group, was similarly designed to harvest information and was used against the government sector.
Whilst Pegasus has been around since 2011, a recent campaign leveraged exploits and vulnerabilities that were patched in February and March 2023. Later, in May 2023, a joint investigation with the Citizen Lab, Amnesty International and other research groups revealed that the exploits had been used against the Armenian civil society to deploy Pegasus between October 2020 and December 2022. They were also used against the civil society in Mexico in 2022, whilst Jamf researchers further identified spyware on devices belonging to European and Middle Eastern users.
Although news on Pegasus has usually received plenty of media attention, especially when it was used against Western countries, this campaign did not receive much coverage from mainstream Western media. Over the past 90 days, there were only 14 reports on the campaign or mentions of Pegasus in the context of zero-days.
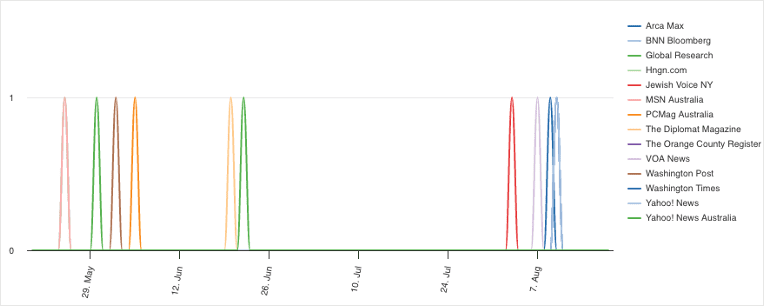
In comparison, there was over double the amount of coverage on the campaign and the exploits amongst security researchers and cyber threat publications, with a total of 33 reports.
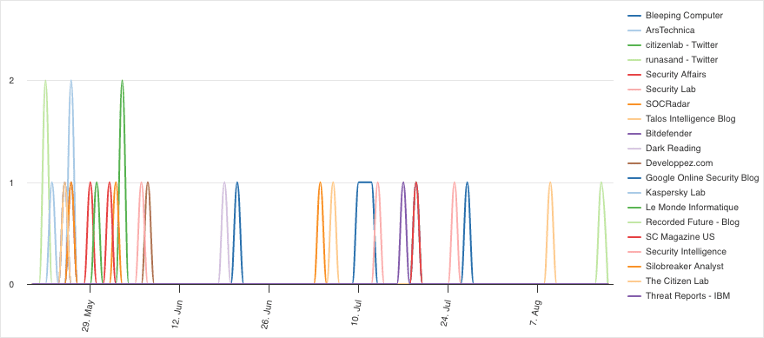
Although this does not show a stark difference in reporting, most of the reports in the mainstream Western media did not reference the campaign itself, but rather mentioned Pegasus in other zero-day contexts. This includes reports on an internal investigation by the Federal Bureau of Investigation regarding its use of Pegasus, and activists suing the Thai government for allegedly using Pegasus against them.
Comparing the coverage of Operation Triangulation and recent Pegasus spyware activity shows that cyber threat publications widely cover such topics, whilst mainstream media from the Five Eyes countries feature less content. One could argue that the activity is in the domain of cyber security and therefore not as relevant to the general media as other topics. However, the two activity sets targeted the government sector and involved zero-day exploits in mobile devices used by billions of individuals – a topic we would expect to receive heightened attention even in mainstream media.
This led us to examine other malicious activity targeting the government sector, as we were curious to what extent major sophisticated campaigns in general receive mainstream media attention.
Storm-0558: Western media coverage on the China-based espionage actor
A recent example of sophisticated nation-state activity is that of Storm-0558, a China-based espionage actor that targeted government organisations. These include high-profile individuals such as the US Commerce Secretary, Gina Raimondo, as well as other State and Commerce Department officials.
Storm-0558 gained access to the organisations’ emails using forged authentication tokens. This was done by acquiring a Microsoft account consumer signing key by exploiting a token validation issue, which several researchers compared to a zero-day. Microsoft has since mitigated the key and blocked activities from the actor, but the company is still under investigation by US authorities in connection to the incident and as part of a larger inquiry into the risks involved in cloud computing.
Between 9th July and 29th July 2023, when the activity was reported, there were 92 reports amongst security researchers and cyber threat publications.
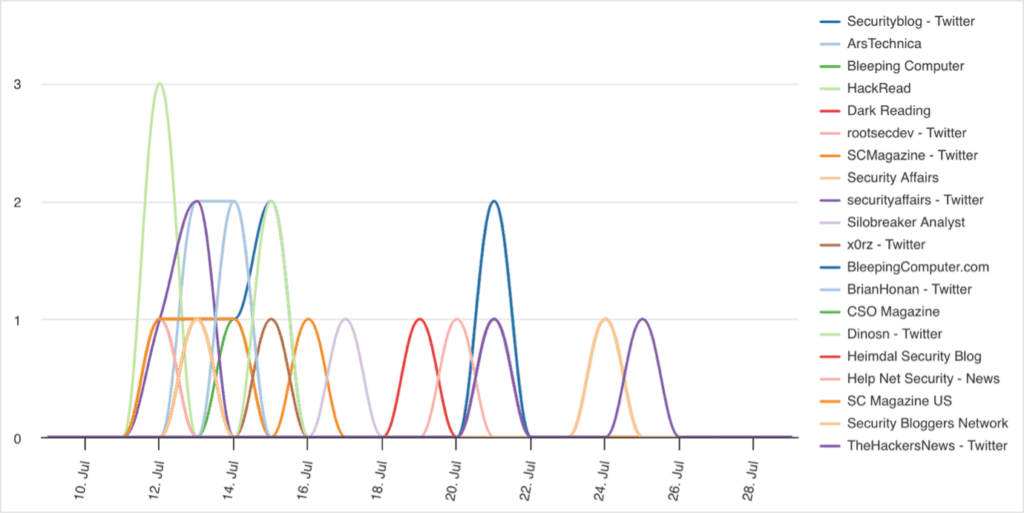
In comparison, there were 294 reports in Five Eyes media, representing over 300% more coverage than that of the researchers.
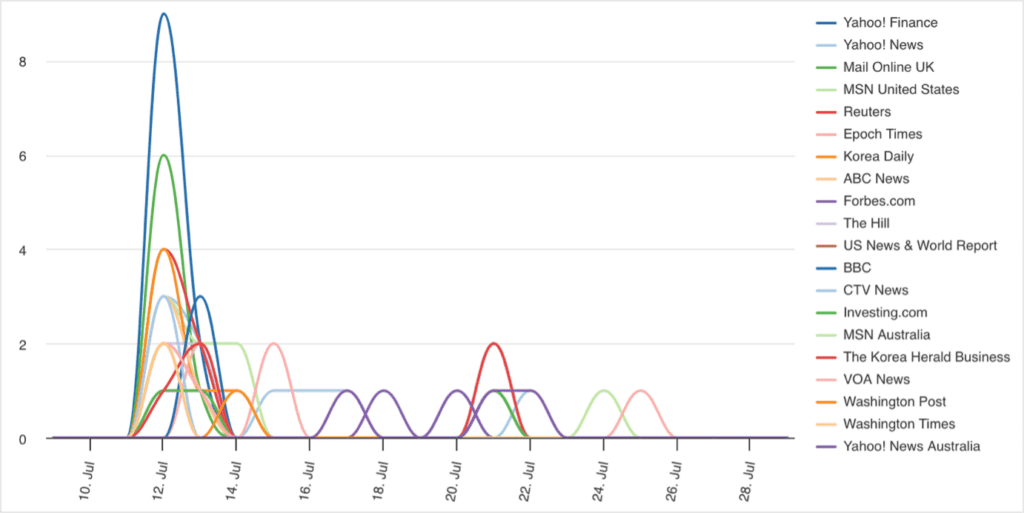
The exact reason for such a high reporting of this campaign in mainstream media is unclear, though it could indicate that mainstream Five Eyes media is more likely to cover nation-state activity targeting the West than other cyber activity, in particular activity originating from Big Four countries, like China. The targeting of high-profile US government individuals likely also contributed to the high amount of reporting in mainstream media.
This left us wondering whether larger campaigns impacting organisations based in Western countries would similarly be reported on more in mainstream media compared to cyber threat publications. To examine this, we looked at the ongoing attack campaign by the Clop ransomware group using a zero-day in MOVEit Transfer to extort hundreds of organisations around the world.
Equal reporting on Clop ransomware gang’s targeting of MOVEit
Reports on the exploitation of MOVEit Transfer began to emerge in late May 2023. Soon after, the Clop ransomware group claimed responsibility for the attacks that enabled them to steal sensitive data from organisations using the vulnerable software.
Over the past 30 days, there were around 5,200 reports on the activity from both mainstream Western media and cyber threat publications, respectively. This shows that at least one large, sophisticated campaign received plenty of mainstream reporting; however, not to an exaggerated extent like that of Storm-0558.
It is not surprising that the campaign has been highly reported on in mainstream media, as the number of victims has risen above 1,100 since the exploitation started. This includes major companies like the BBC, Medibank, Deutsche Bank, Ernst & Young, Shell and Deloitte, as well as multiple US government agencies and departments. The attack further shows how the exploitation of zero-day flaws in a single piece of software can have a wide-reaching and devasting impact on the broader supply chain.
When looking for further campaigns targeting the West, what we noticed was that many of the campaigns we consider to be major generally did not receive much mainstream media attention. Take, for example, the recent exploitation of a zero-day vulnerability in Ivanti’s Endpoint Manager Mobile in an attack against the Norwegian government. News of this campaign barely made it into mainstream Western media, though it was very prominent amongst cyber threat publications. Examples like this highlight a potential bias from our side, where we expect such activity to be more well-known, despite it being a niche subject in a larger context.
Mitigating biases: Use a multitude of sources
Overall, the examples that we examined show that security researchers tend to be more balanced in their reporting. On the contrary, Five Eyes media appear to report less frequently on cyber threats, and if they do, they appear to mostly focus on attacks that have quite a widespread impact, especially if they affect major corporations or government organisations in the West. At the same time, it became evident that cybersecurity remains a niche topic more generally, demonstrating just how important it is to rely on multiple sources to be able to get a holistic overview of any ongoing cyber threats.
A biased coverage, mixed with internal biases, may skew perceptions, result in a narrow focus and cause analysts to miss out on important information. Whilst there are practices that can be implemented to counter internal biases, like broadening or changing the focus of the questions asked, security practitioners should make use of a wide variety of sources to ensure that they work with nuanced information. Silobreaker not only catches information from security researchers, cyber threat publications and mainstream news media, but also automates the processing of such data to make it easier for analysts to stay on top of emerging cyber threats. This enables analysts to obtain a comprehensive picture of APT activity, allowing for more informed and confident decision-making.
To learn more about Silobreaker, request a demo today.

