In recent years, North Korean threat actors have become increasingly sophisticated in their methods, using unconventional tactics to infiltrate systems and exfiltrate data, both for espionage purposes and financial gain. This blog post will discuss two strategies that have raised particular concern, namely the use of malicious Node Package Manager (npm) packages and fake IT worker scams on LinkedIn. These techniques are both targeted and effective, exploiting the trust developers place in open-source software and the professional networks that individuals rely on for career growth and employment opportunities.
LinkedIn IT worker scams
As the leading professional networking platform, LinkedIn is a prime target for threat actors seeking to target high-value individuals in the defence, technology, finance, and cryptocurrency industries. North Korean threat actors continue to deploy sophisticated social engineering techniques to lure professionals into engaging with fake job opportunities. They do this by creating fake recruiter profiles from well-known companies, which are carefully designed to appear legitimate, and use job offers tailored to the target’s background and expertise. Once a victim expresses their interest in the post, the threat actors then contact them with personalised messages, using specific details gathered from the victim’s LinkedIn profile to enhance the authenticity and legitimacy of the scam. The attacker may then offer the victim a ‘job interview’ and encourage them to open a link to a fake company phishing website or to download a malicious attachment disguised as a resume or contract. These scams attempt to exploit the professional nature of LinkedIn, where users tend to trust communications from recruiters or hiring managers. By exploiting this trust, threat actors have been able to gain access to critical information and compromise target networks, often without victims suspecting malicious intent.
Contagious Interview campaign
The Contagious Interview campaign, first discovered by Palo Alto Networks Unit 42 researchers, has been actively targeting job seekers through fake LinkedIn IT worker scams since as early as December 2022. This campaign stands out as one of the most prominent examples of North Korean threat actors leveraging LinkedIn to trick individuals into engaging with malicious job offers. The attackers pose as employers to lure software developers into installing malware through the interview process. The malware enables various types of theft, including cryptocurrency theft. Compromised targets are later used as a potential staging environment for additional attacks, including supply chain attacks. The campaign is also renowned for its use of two new malware families, BeaverTail and InvisibleFerret. BeaverTail is an infostealer malware that hides inside npm packages. It targets cryptocurrency wallets and credit card details and acts as a loader for the InvisibleFerret backdoor.
Around November 2023, the threat actors behind the Contagious Interview campaign have significantly expanded the campaign’s reach by incorporating both Windows installers and macOS applications, increasing the pool of potential victims. The latest version of InvisibleFerret now includes a dynamically updated remote monitoring and management configuration, along with a tailored persistence mechanism for each operating system. In addition to InvisibleFerret, SentinelOne researchers discovered a new macOS backdoor being used as part of the campaign, dubbed FlexibleFerret. The malware impersonates legitimate applications, such as a Google Chrome update, and shows a fake error message upon installation to avoid raising suspicion. Generative artificial intelligence is reportedly also being used to create study guides for fake job interviews, showcasing the evolving sophistication of the attackers and the campaign.
Wagemole campaign
Unlike Contagious Interview, which involves threat actors posing as recruiters, the threat actors behind the Wagemole campaign impersonate jobseekers looking for remote employment with organisations based in the United States and other parts of the world. The aim of the campaign is both financial gain and espionage, with the North Korean government suspected of using the remote workers to finance its weapons programs. The Wagemole campaign likely began as early as August 2022.
The Wagemole campaign has undergone multiple updates, with a new activity cluster, dubbed CL-STA-0237, linked to recent phishing attacks using malware-infected video conference apps. This tactic has also been seen in Contagious Interview activity involving BeaverTail and InvisibleFerret malware, marking a connection between the two campaigns. New domains tied to this cluster also resolve to an IP address connected to the July 2024 MiroTalk campaign. Based on residential IP addresses, the campaign may originate from Laos, marking a shift from the usual IP addresses in China and Russia associated with previous Wagemole activity.
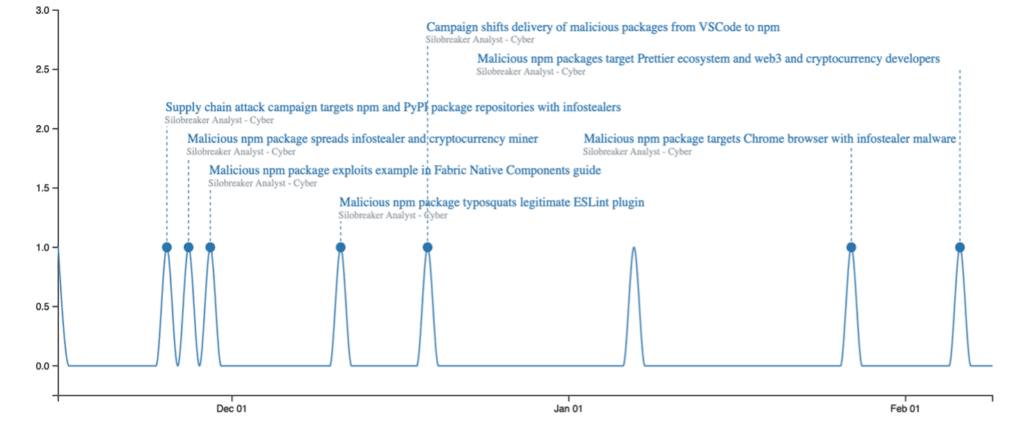
Malicious npm packages
North Korean threat actors have also increasingly leveraged npm packages to distribute malware and malicious JavaScript files to conduct espionage activities. These attacks specifically leverage the trust developers place in npm’s ecosystem, where millions of packages are regularly used in software development. The use of malicious npm packages allows North Korean actors to covertly infiltrate their targets, often focusing on industries tied to critical infrastructure, research, or government agencies, to gain a strategic advantage over foreign adversaries.
By compromising widely used npm packages or publishing malicious packages under typosquatted names, these actors can evade detection and gain access to target systems. Attacks typically start when unsuspecting developers install these seemingly benign packages as dependencies in their projects. Once the malicious package is integrated into the environment, it silently executes malicious payloads and malware designed to steal sensitive data, monitor user activity, or create backdoors for further exploitation. Along with LinkedIn, threat actors behind these attacks have also been reported by GitHub and Phylum.
DEV#POPPER campaign
One notable campaign that has exploited malicious npm packages to target software developers is the DEV#POPPER campaign. This operation uses a multi-stage infection chain, luring victims with fake job interviews and gradually compromising their systems. The attackers pose as interviewers seeking to hire software developers, eventually delivering a malicious ZIP file disguised as a npm package designed to test the applicant. Once the victim executes the npm package, a Python-based remote access trojan is deployed, enabling the attackers to maintain persistence, perform remote command execution, and establish C2 communication.
While DEV#POPPER has primarily targeted victims in South Korea, its reach has expanded to include Europe, the Middle East, and North America. The threat actors behind this campaign have enhanced the malware with advanced FTP functionality, improved obfuscation techniques, and post-exploitation scripts that steal browser-stored passwords and credit card information. These ongoing improvements reflect the campaign’s growing sophistication, positioning it as a serious and persistent threat. Based on its targeting, tactics, techniques, and procedures, the campaign has also been attributed to North Korean threat actors.
Lazarus Group’s Operation Dream Job, Dangerous Password and AppleJeus
The North Korean threat actor Lazarus Group has similarly exploited LinkedIn and the npm ecosystem to target organisations. Several campaigns have been specifically attributed to the group, namely Operation Dream Job, Operation Dangerous Password and Operation AppleJeus. The campaigns have been ongoing since at least 2018, with Japanese organisations one of its prime targets.
Operation Dream Job targets defence industry companies, using hijacked LinkedIn accounts to lure victims into moving the conversation to other messaging platforms, like WhatsApp or Skype. There, the victim is lured into opening a malicious Word document, which installs malware on their devices. As of December 2024, the campaign has also delivered new malware such as CookiePlus, LPEClinet, Charamel Loader, ServiceChanger, and CookieTime, among others.
A similar campaign, dubbed Iranian Dream Job, that mimics the tactics used in Operation Dream Job has also been observed. The campaign, active since at least September 2023 and attributed to the Charming Kitten subgroup TA455, targets the aerospace, aviation, and defence industries. The threat actor employs fake recruiting websites and LinkedIn profiles to distribute ZIP files to targets, which deliver malware via DLL sideloading.
Operation Dangerous Password focuses on cryptocurrency exchanges, where attackers use LinkedIn to convince employees to download a ZIP file containing a malicious executable. Recently, this campaign has expanded to target macOS systems, as well as exploit VHD files, OneNote files, and more. Operation Dangerous Password has also used malicious CHM files to target victims. The files are used to download and execute MSI files, which later leads to the execution of the malware via DLL sideloading.
Operation AppleJeus also targets cryptocurrency users and organisations, providing LinkedIn users with a Telegram link that leads to the installation of a malicious MSI file disguised as a cryptocurrency exchange tool. Examples of tools delivered include fake versions of the JMTTrading and UnionCryptoTrader macOS applications, as well as a series of trojanised apps collectively dubbed TraderTraitor. While the tactics used in the campaign have changed overtime, the overall aim of delivering fake cryptocurrency apps remains the same.
The rise of North Korean state and non-state actors utilising LinkedIn IT worker scams and malicious npm packages represents a growing and evolving threat. Despite sanctions aimed at deterring these activities, such measures have failed to significantly stop threat actors. Instead, threat actors continue to refine their tactics and continue to successfully infiltrate organisations and steal sensitive data. As these campaigns expand and grow more sophisticated, it is crucial for individuals and organisations to remain vigilant.
Silobreaker can help organisations stay informed about ongoing campaigns and keep security teams up-to-date on the latest social engineering techniques. To find out how, get in touch here.

