The group behind the now-infamous Clop ransomware has arguably succeeded in making a name for itself as one of the biggest cybersecurity threats organisations are currently facing. In 2023 alone, Clop has conducted two mass exploitation campaigns, both targeted at managed file transfer services. These types of supply chain attacks are nothing new for Clop, though, who seem to be making it a habit to exploit unknown vulnerabilities in such software in the hopes of a bigger pay out.
Clop ransomware’s latest victim: MOVEit Transfer
At the end of May 2023, Progress Software warned of the active exploitation of an SQL injection vulnerability, tracked as CVE-2023-34362, in its MOVEit Transfer software. By early June, Clop claimed they were responsible for the exploitation, stating that they managed to steal data from hundreds of companies. Since then, numerous companies and government agencies have disclosed being impacted, and on 14th June, the group began naming some of its victims on its data leak site.
Mandiant’s analysis of this most recent Clop hacking spree revealed the use of a custom web shell, called LEMURLOOT, that was used to steal data in the attacks. Kroll researchers additionally found that the group had likely been experimenting with ways to exploit the vulnerability since 2021, and testing different ways to collect and extract sensitive data since April 2022.
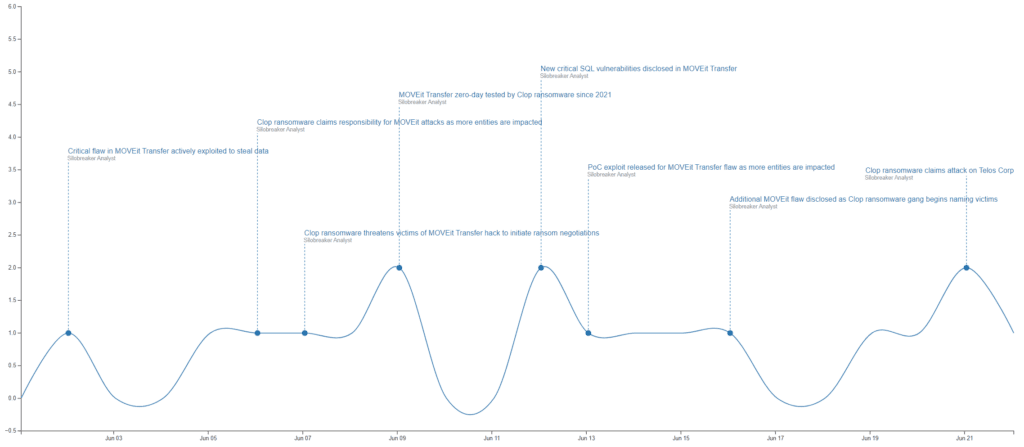
Timeline of headlines as the incident unfolded.
Clop’s previous supply chain victims: GoAnywhere MFT, Accellion FTA, SolarWinds Serv-U
The exploitation of file transfer services is not new to Clop, but rather it seems to be one of their preferred methods of operation after phishing. The gang was also behind the mass exploitation of a zero-day in Fortra’s GoAnywhere Managed File Transfer (MFT) that began in early February 2023. Additionally, the group exploited a similar zero-day in Accellion’s File Transfer Appliance (FTA) in December 2020 and a zero-day in SolarWinds Serv-U Managed File Transfer and Serv-U Secure FTP in 2021.
Both the most recent MOVEit Transfer, and the previous Accellion FTA exploitation attacks occurred just around a significant holiday. For MOVEit, the attacks were launched during the Memorial weekend in the United States, while the Accellion FTA attack happened during the Christmas holiday. The timing of such attacks is not random, but rather the threat actors expect staffing to be at a minimum during these times, with security likely at reduced levels compared to the rest of the year.
Though the Accellion, GoAnywhere and MOVEit campaigns did not involve any encryption, a large amount of data was stolen from numerous companies. In the Accellion and GoAnywhere campaigns, Clop contacted each of its victims in the hopes of negotiating a ransom payment. In the case of MOVEit Transfer, Clop instead told victims to contact them directly for negotiations. As many companies have now been named on their data leak site, it can be assumed that several refused this request.
Danger of supply chain attacks
This type of supply chain attack can have a devastating impact, not just on the initial victim company, but also on its clients and partners. The GoAnywhere campaign saw the data of over 130 companies compromised, with the number believed to be significantly higher in the MOVEit campaign. While these companies must deal with the fact that some of their proprietary data likely ended up in the hands of the criminals, each of these impacted companies also have a large number of customers that are simultaneously impacted. Though many victim companies may try their best to inform any impacted third parties, it is not guaranteed that everyone impacted will be informed directly.
This is why it is important to proactively monitor any supply chain risks, be it to keep track of any incidents that have impacted a third-party provider or conduct a more general analysis of any vulnerabilities or cyber threats relevant to a specific industry.
History of Clop ransomware
Clop ransomware first emerged in 2019 and was later found to be the work of financially motivated threat actor FIN11. The group in turn is believed to be a subset of TA505. FIN11’s toolset additionally includes FlawedAmmyy, FRIENDSPEAK and MIXLABEL. Throughout the years, Clop’s sophistication has grown, with the ransomware strain being modified and improved continuously. Its operators initially relied on phishing emails as their initial access vector and would only encrypt data. From 2020 onwards, the group began exploiting zero-days and stealing data from victims prior to encryption. This year has seen a slowdown in deployment of the ransomware, with the Clop gang appearing to have shifted towards a data extortion-only model.
In mid-June 2021, Ukraine’s Cyber Police announced the arrest of multiple members and a takedown of several servers used for the group’s operations. The arrests were part of the global Operation Cyclone initiated by authorities from the United States and South Korea. The arrested individuals are not believed to be any of the core members, but rather individuals tasked with laundering the proceeds made by the gang. This is also evident in the group’s rapid return following the arrests, with new victims claimed within a week of the arrests.
To date, Clop remains a credible threat to organisations across all industries. Some of the gang’s top targets include financial services, retail, telecommunications, healthcare and transportation. Though the threat actors claimed to have deleted any data from the government, military, and children’s hospitals in their latest hacking spree against MOVEit, such statements cannot always be trusted.
Having the latest knowledge and accurate intelligence about ransomware strains is crucial for organisations looking to protect against these attacks across their supply chain. Click here to learn more.